Merkle Trees
Here you can find examples on how we create the Merkle trees. In all examples we will use the SHA-256 hash function.
First Example
In the first example we will use a Merkle tree with one leaf.
Alice wrote her thesis and she wants to prove that she finalized it before the deadline. She hashes her document and submits the hash using our API.
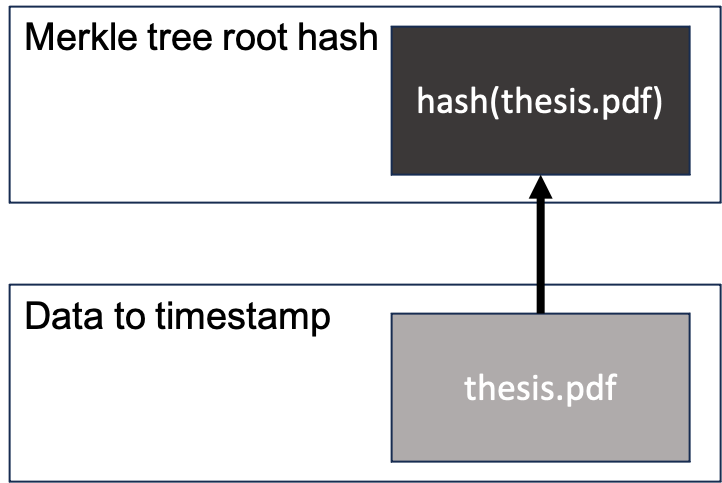
If we don't receive any other hash, Alice's hash will be the only hash in the Merkle tree.
// Alice's thesis hash is 52a0412dfafead865bc77b315c88b5de35edfc2d1b7142db1d589dcd687eee87
sha256(thesis.pdf) = 52a0412dfafead865bc77b315c88b5de35edfc2d1b7142db1d589dcd687eee87
In this case, the root hash is the same as the leaf hash. A transaction containing the root hash 52a0412dfafead865bc77b315c88b5de35edfc2d1b7142db1d589dcd687eee87 will be broadcasted to a blockchain.
Second Example
In the second example we will use a Merkle tree with two leaves.
Alice wrote her thesis and she wants to prove that she finalized it before the deadline. Bob wants to prove his audio recording with predictions about an event existing before the event. They both hash their file and submit the hash using our API.
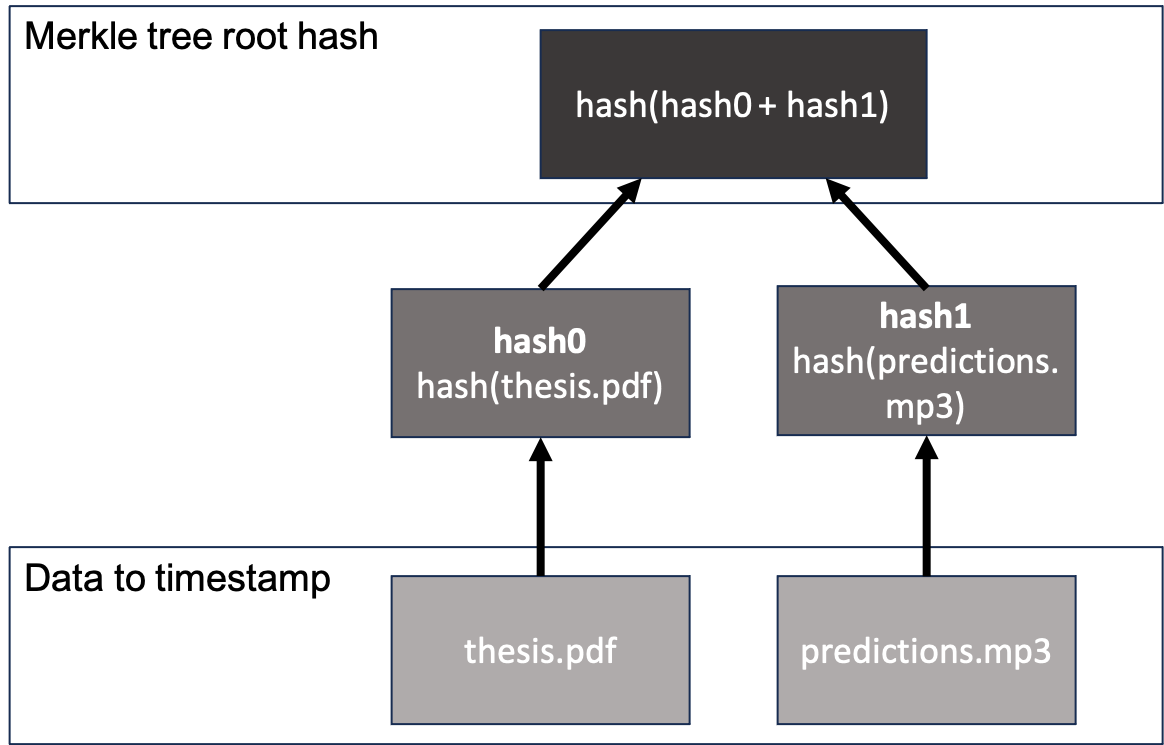
With the two hashes we create a Merkle tree. A transaction containing the root hash will be broadcasted to a blockchain. Instead of creating a Merkle tree and broadcasting the root hash we could create a separate transaction for each hash like the previous example. However, this approach would cost us double the transaction fees.
// Alice's thesis hash is 52a0412dfafead865bc77b315c88b5de35edfc2d1b7142db1d589dcd687eee87
sha256(thesis.pdf) = 52a0412dfafead865bc77b315c88b5de35edfc2d1b7142db1d589dcd687eee87
// Bob's audio recording hash is 34f1b141903c0935b3b29884cb421bb1f8e202e32866572dd03a28d2c2a93ce6
sha256(predictions.mp3) = 34f1b141903c0935b3b29884cb421bb1f8e202e32866572dd03a28d2c2a93ce6
// The root hash of the Merkle tree is
sha256(sha256(thesis.pdf) + sha256(predictions.mp3)) = cd1dc61a232405cf2af01ae6a87f90e24e82bda17224f0576435e3249012d115
// Or
sha256(52a0412dfafead865bc77b315c88b5de35edfc2d1b7142db1d589dcd687eee8734f1b141903c0935b3b29884cb421bb1f8e202e32866572dd03a28d2c2a93ce6) = cd1dc61a232405cf2af01ae6a87f90e24e82bda17224f0576435e3249012d115
Third Example
In the third example we will use a Merkle tree with three leaves.
Alice wrote her thesis and she wants to prove that she finalized it before the deadline. Bob wants to prove his audio recording with predictions about an event existing before the event. Charlie wants to timestamp the existence of his cooking recipe. All three hash their file and submit the hash through our API.
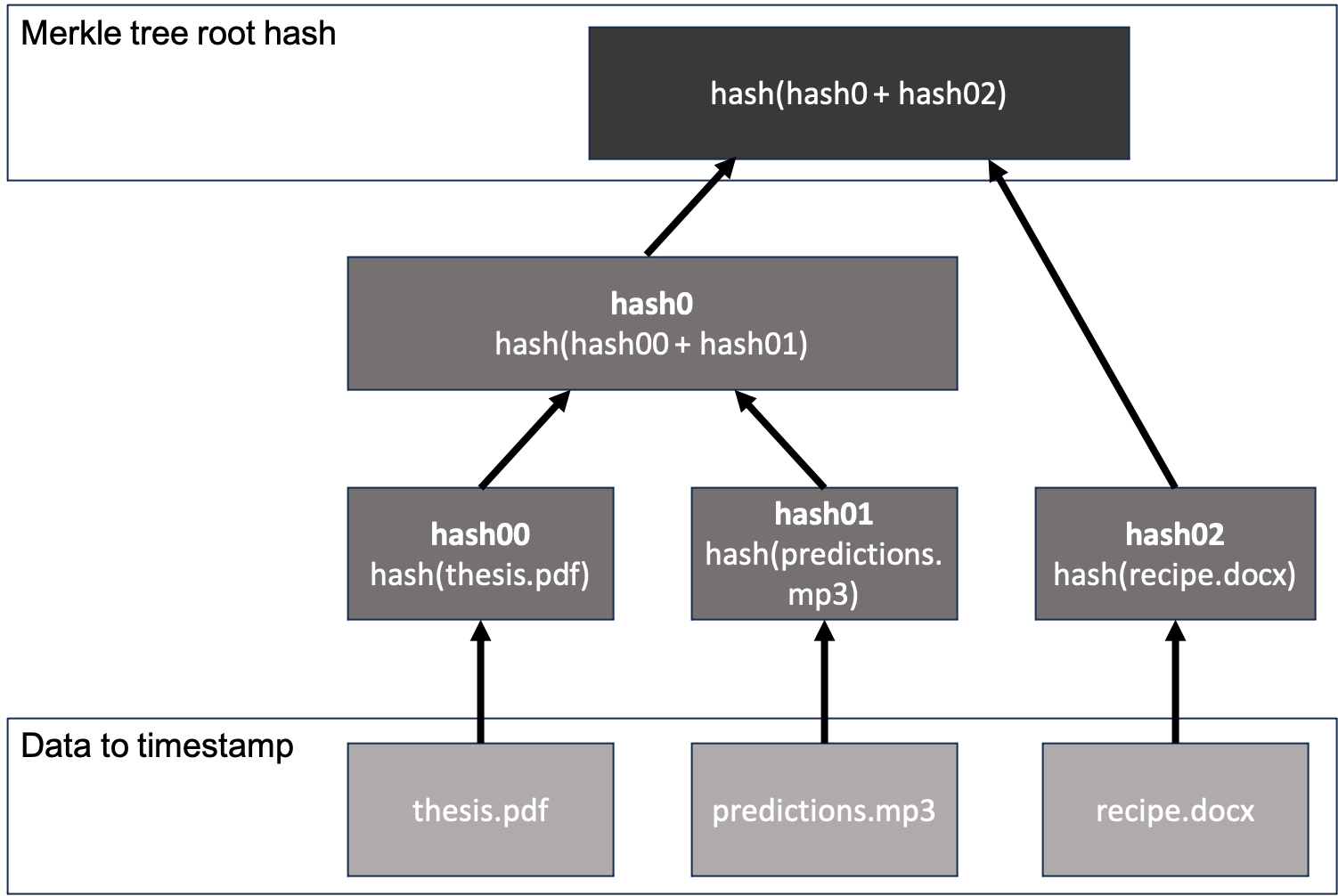
// Alice's thesis hash is 52a0412dfafead865bc77b315c88b5de35edfc2d1b7142db1d589dcd687eee87
sha256(thesis.pdf) = 52a0412dfafead865bc77b315c88b5de35edfc2d1b7142db1d589dcd687eee87
// Bob's audio recording hash is 34f1b141903c0935b3b29884cb421bb1f8e202e32866572dd03a28d2c2a93ce6
sha256(predictions.mp3) = 34f1b141903c0935b3b29884cb421bb1f8e202e32866572dd03a28d2c2a93ce6
// Charlie's recipe hash is 605d83faa093de0649a0496408619b602f49e33be381a9bbf519703243698687
sha256(recipe.docx) = 605d83faa093de0649a0496408619b602f49e33be381a9bbf519703243698687
// The hash0 is
sha256(52a0412dfafead865bc77b315c88b5de35edfc2d1b7142db1d589dcd687eee8734f1b141903c0935b3b29884cb421bb1f8e202e32866572dd03a28d2c2a93ce6) = cd1dc61a232405cf2af01ae6a87f90e24e82bda17224f0576435e3249012d115
// The root hash of the Merkle tree is
sha256(cd1dc61a232405cf2af01ae6a87f90e24e82bda17224f0576435e3249012d115605d83faa093de0649a0496408619b602f49e33be381a9bbf519703243698687) = ce4b0a7f281f2d27b4a4886b480f104c760f560f95355bde9edcf848ee49985f
Forth Example
In the fourth example we will use a Merkle tree with four leaves.
Alice wrote her thesis and she wants to prove that she finalized it before the deadline. Bob wants to prove his audio recording with predictions about an event existing before the event. Charlie wants to timestamp the existence of his cooking recipe. Dennis wants to timestamp his poem. All four hash their file and submit the hash through our API.
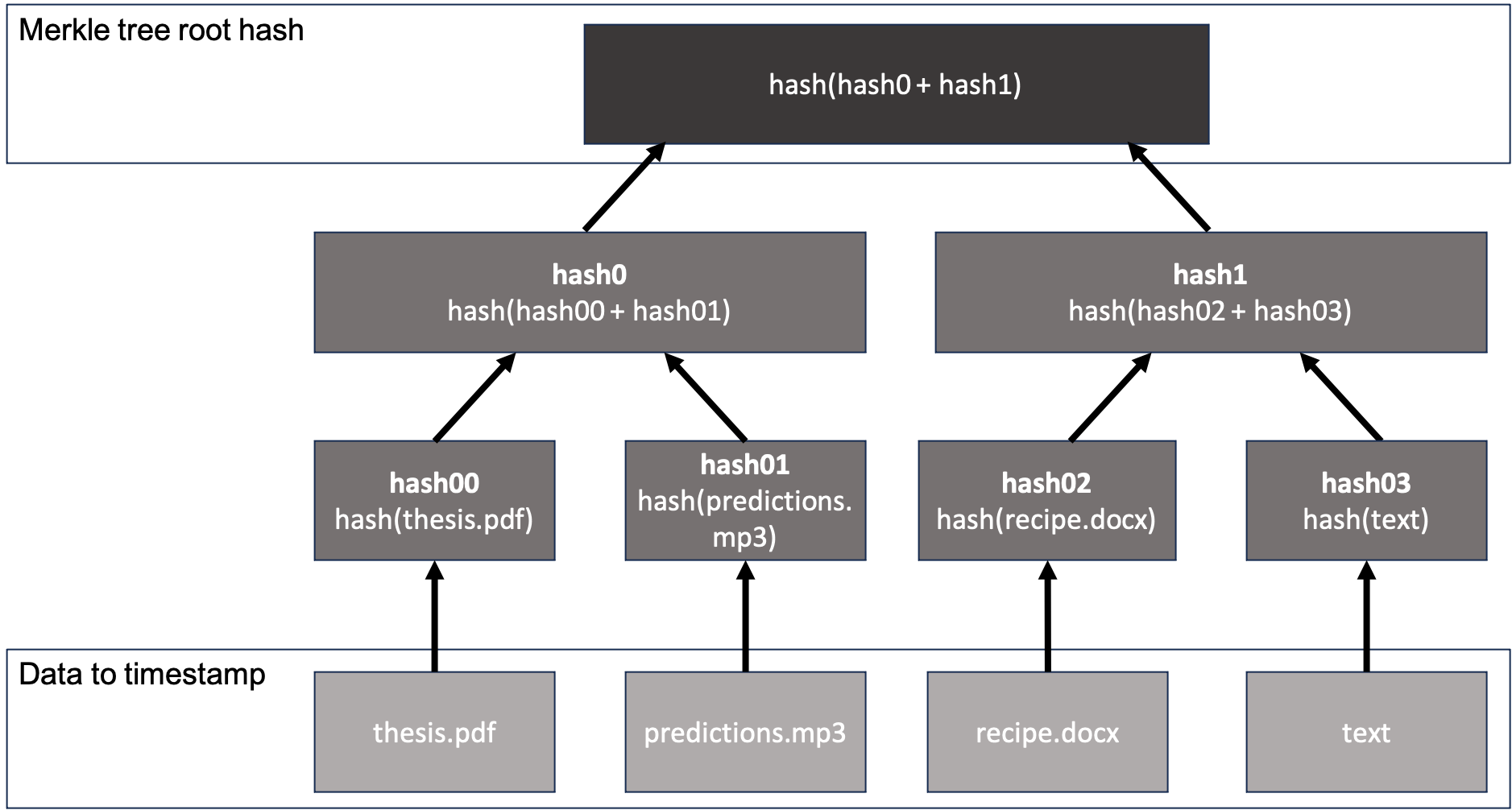
// Alice's thesis hash is 52a0412dfafead865bc77b315c88b5de35edfc2d1b7142db1d589dcd687eee87
sha256(thesis.pdf) = 52a0412dfafead865bc77b315c88b5de35edfc2d1b7142db1d589dcd687eee87
// Bob's audio recording hash is 34f1b141903c0935b3b29884cb421bb1f8e202e32866572dd03a28d2c2a93ce6
sha256(predictions.mp3) = 34f1b141903c0935b3b29884cb421bb1f8e202e32866572dd03a28d2c2a93ce6
// Charlie's recipe hash is 605d83faa093de0649a0496408619b602f49e33be381a9bbf519703243698687
sha256(recipe.docx) = 605d83faa093de0649a0496408619b602f49e33be381a9bbf519703243698687
// Dennis' poem hash is 8f434346648f6b96df89dda901c5176b10a6d83961dd3c1ac88b59b2dc327aa4
sha256(text) = 8f434346648f6b96df89dda901c5176b10a6d83961dd3c1ac88b59b2dc327aa4
// The hash0 is
sha256(52a0412dfafead865bc77b315c88b5de35edfc2d1b7142db1d589dcd687eee8734f1b141903c0935b3b29884cb421bb1f8e202e32866572dd03a28d2c2a93ce6) = cd1dc61a232405cf2af01ae6a87f90e24e82bda17224f0576435e3249012d115
// The hash1 is
sha256(605d83faa093de0649a0496408619b602f49e33be381a9bbf5197032436986878f434346648f6b96df89dda901c5176b10a6d83961dd3c1ac88b59b2dc327aa4) = 80a9e67a10e90a82c14ef391b784f3e941cb42a7cff7a98e10256b5c3240a816
// The root hash of the Merkle tree is
sha256(cd1dc61a232405cf2af01ae6a87f90e24e82bda17224f0576435e3249012d11580a9e67a10e90a82c14ef391b784f3e941cb42a7cff7a98e10256b5c3240a816) = 37f6a60ad1e57f49cf2184e5062caac561befaffdf37649a8ce336266631506f